Dave Kearns wrote a column at Network World about my book, Digital Identity. The focus of the column is the identity policy templates I wrote for the book. They've been getting a lot of attention, if downloads are any indication.
I actually wrote them because I found as I wrote the chapter on policy that it was almost impossible to do without some examples. I had a few that we'd done at Utah and some samples off the 'Net here and there, but nothing complete and coherent.
|
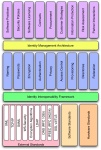
Digital identity policy stack (click to enlarge)
|
The idea behind the policies is that identity is foundational to many other things, including computer and network security. Thus, there ought to be identity policies that are separate from and serve to enable good security policy. The picture at the right shows how this works. The blue boxes in the middle are the identity policies. Security policies are just one of the top boxes. The bottom tier is the interoperability framework--a completely different discussion.
The policies I wrote include the following:
- Naming and Certificates WORD | PDF
- Passwords WORD | PDF
- Encryption and Digital Signatures WORD | PDF
- Directories WORD | PDF
- Privacy WORD | PDF
- Authentication WORD | PDF
- Access Control WORD | PDF
- Provisioning WORD | PDF
- Federation WORD | PDF
- Data Confidentiality Agreement WORD | PDF
I wrote these are Word documents since the idea is that these are templates that you can download and tailor to your own organization. Over the coming weeks I'll write an article describing each one of these as well as some other identity policy considerations.